Automation is the hidden key to a successful IoT implementation. To see why, it’s important to understand the current profile and strategic direction of IoT projects.
In Nemertes’ 2019-2020 IoT research study, we found that 68% of participants were in proof-of-concept (POC) or early production (less than 25% complete) stages of their IoT rollouts. Half of those expected both device counts and project counts to grow at 25% or more per year over the next 3 years. And successful companies (ones that scored in the top 20% for revenue generated, cost savings, or business process improvement) were twice as likely as the rest to anticipate hypergrowth (100% or more per year).
In sum, the wave of IoT initiatives is just beginning, and is nowhere near cresting. Enterprises are seeing extreme growth on two dimensions: device count for existing projects, and the number of IoT projects in the portfolio.
This means that IoT is rapidly getting past the point at which manual control, management, configuration, and security is feasible.
In IT parlance, the devices (and projects) are moving from pets to cattle: transitioning from the need for focused care and attention (pets) to the need for streamlined and scalable systems and processes (cattle).
But what does it mean to “automate” IoT? There are two main areas for automation. The first is visibility. This means knowing how many devices there are in an IoT implementation (auto-inventorying), knowing how they behave, and knowing what behavior is normal vs anomalous.
This information must be collected automatically, and analyzed effectively, to quickly be able to spotlight systems that are behaving anomalously, either due to operational issues or cybersecurity attacks. In cybersecurity environments, we refer to automating the behavioral analysis as “behavioral threat analytics”.
Visibility is critical, but it’s only part of the equation. The second part is automated configuration and policy enforcement. IoT devices must be configured, and the configurations patched and updated based on a standardized policy. And if devices need to be shut down (e.g. if they’ve been infected with bots) that should happen automatically, based on policy triggers. Alerts and manual overrides can be configured, to maintain human control, but in large, complex IoT installations, it’s critical to contain attacks quickly, and have human intervention at the forensic stage.
Why does all this functionality require automation? Quite simply, because of scaling issues. As individual IoT projects blossom, and the number of projects proliferates, doing these things manually is no longer feasible.
The blueprint for developing an effective automation strategy is therefore this: First, think in terms of a developing horizontal IoT architecture that addresses the key issues of management, control, and cybersecurity for all IoT projects, regardless of use cases. (See figure 1)
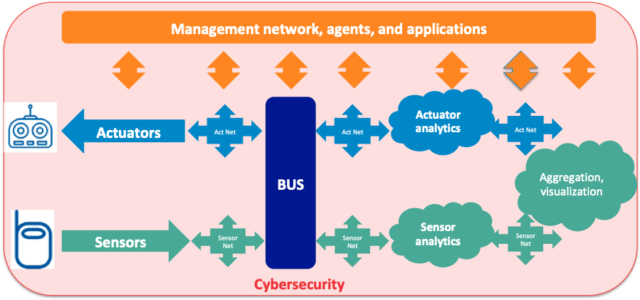
Second, start by ensuring visibility into every IoT implementation. That means having tools in place to autodetect IoT devices and automatically analyze their behavior, reporting information into a common dashboard.
Third, put in place a policy-based approach to configuration, management, and security. That means having an automated way to take action based on defined policies.
Finally, enhance the automated configuration and management with human alerts and overrides where necessary, to maintain control over the entire infrastructure, automation and all.
The bottom line: The natural consequence of successful IoT projects is growth, and growth drives the need for effective automation. IoT technology practitioners (whether IT or OT) should make sure their IoT initiatives include an IoT automation strategy.
Interested in hearing more? Attend the Ordr and Nemertes webinar on IoT automation on June 9 – “Fast, Secure, Scalable: Why IoT Needs Automation to Succeed”. Register here.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud



