On Oct 28, 2020, the Cybersecurity and Infrastructure Security Agency (CISA) along with the Federal Bureau of Investigations (FBI) and Health and Human Services (HHS) announced an increased and imminent cyberthreat to the Healthcare and Public Health Sector. This warning comes on the heels of increased ransomware incidents in the last few months and includes information on Conti, TrickBot, BazarLoader and new Indicators of Compromise (IOCs). As healthcare continues to grow as a reliable source of income for threat actors because of the necessity to protect patient care, ransomware campaigns will continue to proliferate.
Jeff Horne, Chief Security Officer at Ordr, provides insight into the latest wave of ransomware with a series of articles:
- Ransomware in Healthcare Providers and Healthcare Delivery Organizations – Tactics, Techniques, and Procedures and Recommendations of How to Triage
- A Primer on Preparing for and Responding to Ransomware for Users of IoT and IoMT
Threat Summary
Ransomware has been around for decades and while the recent evolution in the past few years has transformed into more of a service – yes, Ransomware-as-a-Service (RaaS), it can be attributed to one of the reasons there is a 25 percent increase in attacks from Q4 2019 to Q1 2020 and a 715% year-over-year increase in detected – and blocked – ransomware attacks and the average payment increased by 33%.
The distributed nature of the ransomware developer and the affiliates makes it more lethal than ever.
Ransomware developer: Who creates custom malicious code, and capabilities like lateral movement tools and scripts, and including exploit code that is sold to a ransomware affiliate for a fee or share in eventual ransom after a successful attack.
Ransomware affiliate: Starts a hosting site with custom exploit code. Identify targets and send the exploit code typically by phishing email or as an attachment.
Victim: Falls victim to the exploit code.
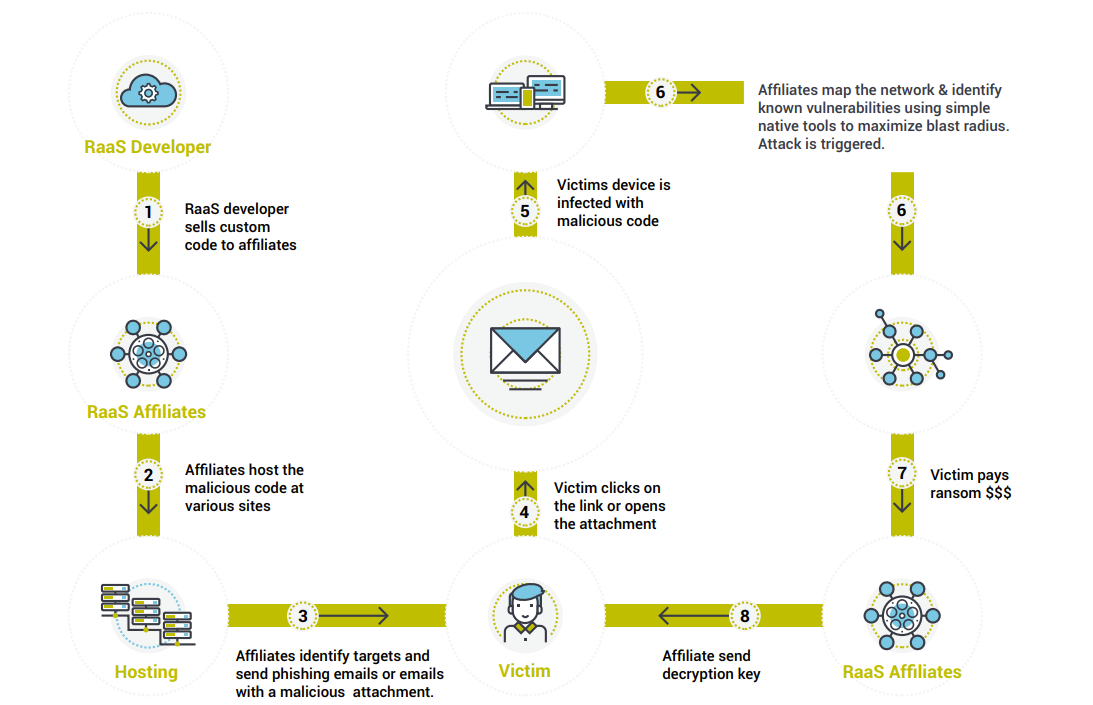
There are several RaaS types identified by security experts. Some examples are Sodinokibi, Ryuk, Mamba, Phobos, Dharma, Snatch, etc. It is worth noting that in the actual ransomware code is usually the last piece dropped in the infection life cycle giving hope that this can be prevented. The infection usually starts with Trojans like Trickbot, will go through the baking process where the RaaS affiliates monitor and map out the network and any existing vulnerabilities and then drop the actual ransomware code.
Ordr recommendation for defense against RaaS:
There are several recommendations given by security experts. Ordr compiled the Mitigation plans and policies from the CISA advisory and others, mapped it to the NIST cybersecurity framework.
Identify
Insightful asset management: Asset management of all the network connected assets is the first step towards defense against any threats. Insightful asset management is not about maintaining a list of IP addresses or serial numbers but a very detailed inventory containing – What the device is, where it is located, Operating System details etc. Ordr passively detects all the network connected devices creates a database with make, model, OS, location and other detailed information.
Continuous monitoring: Continuous monitoring is key for any good asset management and security programs. With the proliferation of IoT devices continuous monitoring is key to the protection of the entire Organization. A device that is not supposed to be in the network need to be detected right away and appropriate action need to be taken. Ordr detects a device the moment it is active in the network and records the same. Ordr can quarantine or disconnect a device from the network with a click of a button.
Knowledge of what is in your control and more importantly what is not: Organizations usually maintain the inventory of the assets that they control. What is largely missed are the assets that are not “owned” by the organization but still uses the critical resources of the organization – third-party managed network, vendor devices, devices and software under vendor qualification etc. Ordr detects all these devices and gives a very easy way to identify these unmanaged devices with ease.
Asset criticality: Knowing and protecting critical assets is a critical part of the security program. For healthcare Ordr provides Clinical risk metrics that helps prioritize and secure the most critical assets.
Protect
Security awareness: Awareness is key to any security program. This process should cover topics from identifying malicious emails to social engineering risks. Make sure that Security awareness campaign is an ongoing process.
Understand vulnerability threat posture: Understand the existing vulnerabilities of all the devices and software in the network. Most of the ransomware damage is done using the existing vulnerabilities. One of the vulnerabilities identified as a major exploitation vector is CVE-2020-1472. Ordr identifies devices that are impacted by this vulnerability. Ordr in combination with any popular vulnerability detection software like Tenable or Rapid7 provide a complete picture of IoT specific and application vulnerabilities. With the combination of critical infrastructure score, organization knows how to prioritize the never-ending patching programs.
Bring unmanaged devices under compliance: In almost all deployments Ordr found devices that the security teams never knew existed. These range from someone plugging in some device into the corporate network, contractor/vendor devices to third party managed networks. Ordr can easily identify these devices so that appropriate action can be taken to bring these devices in compliance.
Understand active threat posture: Active threats are different from vulnerabilities. Ordr has an inbuilt IDS engine that can detect East to West threat propagation. Understanding the criticality of the device along with the evidence of vulnerability exploitation is very critical. Typical Firewalls don’t catch East to West threat propagation. Ordr detects and reports the East to West threat propagation that reduces the threat response time.
Monitor active communications: No one wants their device to talk to the bad websites. Ordr detects these activities right away and triggers an alarm.
Backup and encryption: As a standard practice, perform regular backup and encryption.
Be proactive: These new attacks try to understand the network and the connectivity details to cause maximum damage. Microsegmentation is a sure way to protect the network from the ransomware attacks as the threat exposure is minimized. Ordr makes microsegmentation easier and a reality.
Detect
Make sure standard security practices are up-to-date: Make sure that all the security measures you have in place like end-point protection software and threat feed information are up-to-date. Provide continuous security education to all the users including vendors and contractors.
Logging: Make sure that you have the logs of all transactions. Ordr records all network transactions over the network. This will help immensely for any forensic activities.
User to device mapping: Its critical to understand who is using what devices and what they are doing with those devices. Ordr helps map user to device mapping and device communication mapping.
Communication patterns: Understanding device to device communication patterns and blocking unnecessary or unexpected communication is another step towards protecting the infrastructure. One of the exploitation vectors for the recent ransomware attacks is the open RDP port 3389. Ordr provides an easy way to identify devices that are communicating over port-3389. User can then decide if this communication is expected or not and if the RDP port itself need to be changed.
Respond
Incident response: Develop a plan to respond to an incident. Ordr helps identify the blast radius, understand the impacted applications and users to come up with an effective threat incident response plan.
Recover
Restore: With the backup and encryption mechanisms in place, restore the data.
Verify: Make sure that the suspect hardware software is not used in the future. Ordr continuous monitors the network for the devices and will let the user know about any vulnerable devices coming back into the network.
Report: Report the incident to appropriate authorities as designated by response and discloser policies.
In summary RaaS has no prescriptive solutions. This can be prevented by following the recommendations by Ordr and other authoritative sources. In the battle between good and evil always good triumphs – We just need to know the exploitation vectors, vulnerability posture of the organization and the active threat posture of the organization. We hope our recommendation will help organizations to continue their business and discourage bad actors from doing malicious activities.
For more information on how Ordr can help you identify and manage vulnerabilities for any connected device, please contact info@ordr.net.

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud



