With the holiday season in full effect, retailers like Walmart and Amazon are rolling out the Deal of the Day. Well, with these deals, comes a great cost savings, but what we also need to take in to account are the risks of these devices. While it is probably fine (although not encouraged) if they are deployed at home, putting these devices on your organizations corporate network can be far more dangerous.
There has been a recent spike in these types of routers being plugged into corporate networks and most of the time by employees who want to either extend the ethernet ports or have their own private network. With the router acting as a gateway NAT-ing all the devices behind it, this becomes an untracked shadow network. Traditional endpoint detection tools cannot detect these types of devices and the potential dangers.
Take the example of the recent reports of the $30 Wi-Fi routers sold at retailers like Walmart and Amazon. Researchers found that these routers contained hidden backdoors and are being exploited by the Mirai botnet. The routers with the reported security hole are the Jetstream router that can be easily purchased, with no disclaimer. These critical vulnerabilities allow threat actors to remotely control the routers as well as any device connected to that network and monitor all the traffic coming through that router. This constant surveillance on the shadow network can critically endangers the whole network. Additionally, the Wavlink routers contain a script that lists nearby Wi-Fi networks and could connect to those networks with the factory passwords. This can have a cascading effect with the attacker slowly and patiently expanding the blast radius.
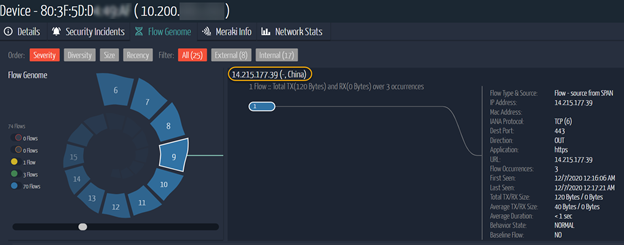
Ordr installed these two routers in our lab environment and almost instantly noticed port-443 connection communicating to known Chinese domains.
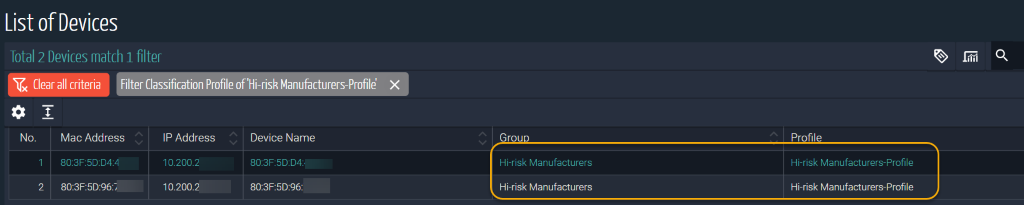
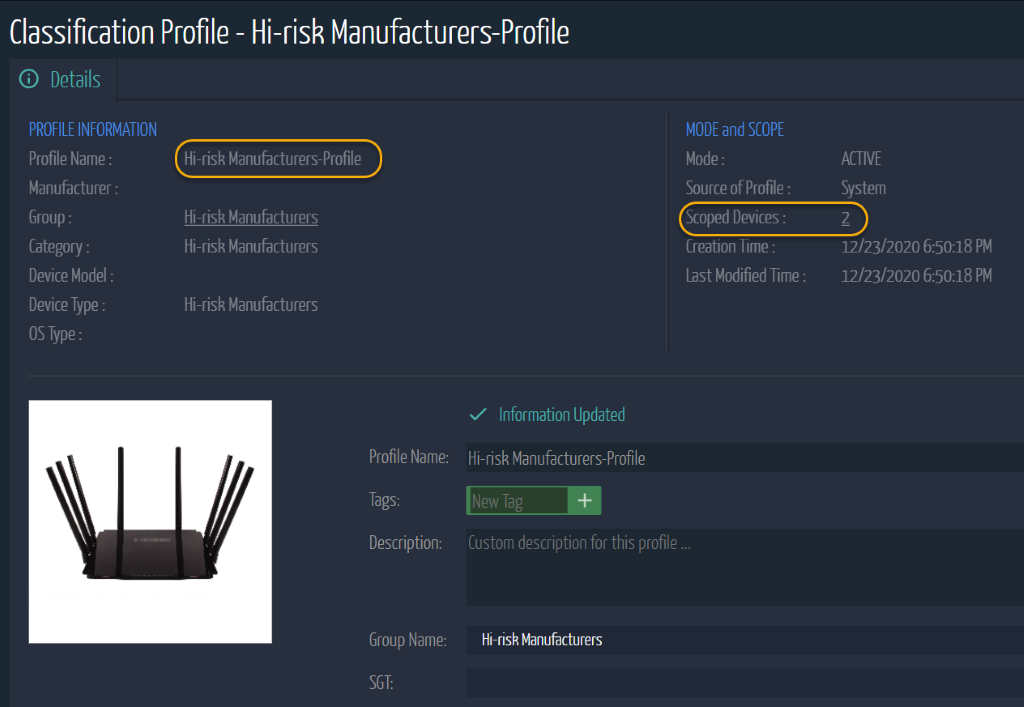
With Ordr, these devices can be easily identified, classified and added to the “Hi-risk Manufacturers” profile.
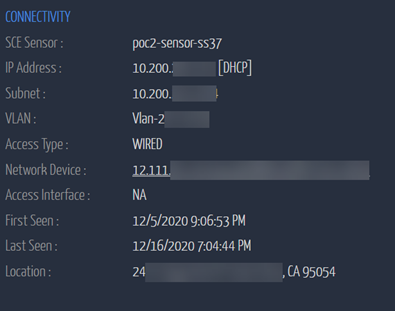
The next challenge is to physically locate these devices so that this can be investigated and removed. Ordr provides device location and also physical connectivity information so that this device can be tracked, and the appropriate workflow is supported.
Identifying these rogue devices is important in protecting your network infrastructure. With Ordr’s ability to see all connected devices via DPI and support massive network infrastructures through AI/ML to classify these devices at scale, then automate policy generation, we can help our customers discover, baseline, and secure their environments.
For more information on how Ordr can help you identify and manage vulnerabilities for any connected device, please contact info@ordr.net.

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud



