On July 14, 2020, the Department of Defense (DoD), General Services Administration (GSA), and National Aeronautics and Space Administration (NASA) published in the Federal Register the interim rule, “Federal Acquisition Regulation: Prohibition on Contracting With Entities Using Certain Telecommunications and Video Surveillance Services or Equipment” that requires federal agencies, including Universities to certify that they do not use telecommunications equipment or services produced or provided by the following Chinese companies or any subsidiary or affiliate of those entities,
- Huawei Technologies Co.
- ZTE Corp.
- Hytera Communications Corp.
- Hangzhou Hikvision Digital Technology Co.
- Dahua Technology Co.
Included in the interim rule are the entities that the Secretary of Defense reasonably believes to be owned, controlled or otherwise connected to the Republic of China government. This rule impacts a range of industries like healthcare, education, automotive and aviation. As organizations look to identify all telecommunications equipment on their network, Ordr can quickly help them do so.
Compliance Made Easy with Ordr
In the interim rule, there is a section that calls for corporate enterprise tracking. Within Ordr, we have worked to create a workflow that will enable organizations to adhere to the actions needed for compliance.
Step 1
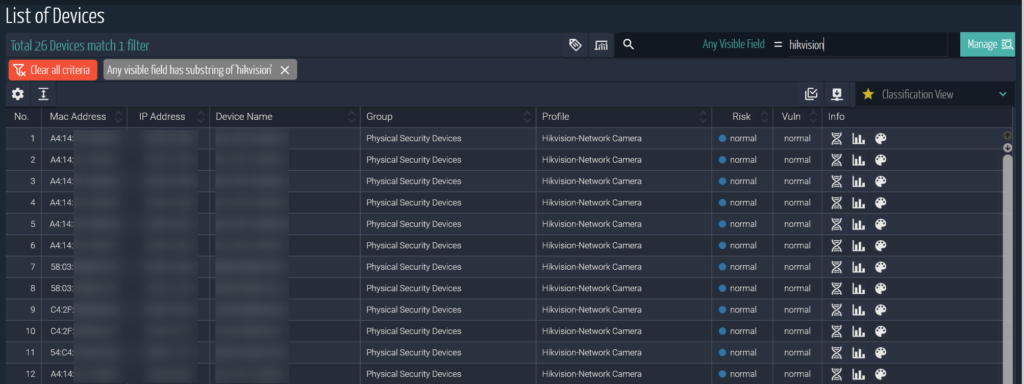
Without any interruptions to the network, Ordr passively detects prohibited devices and simplifies the ability to search for these devices in the UI. In addition to the devices that are clearly marked by the manufactures above, those manufactures also OEM their products which make it infinitely more complex without a solution like Order. For example, Philips often uses Hikvision cameras in their eICU product. Ordr identifies these products with ease, irrespective of the brands.
Step 2
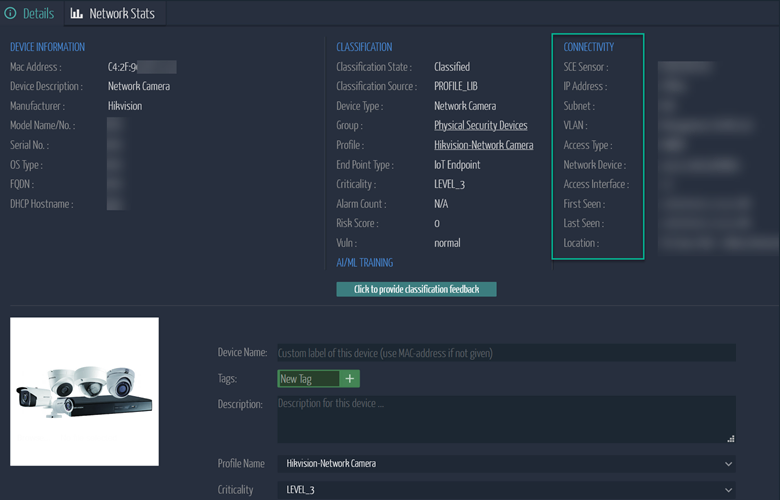
Identify the physical location of these prohibited devices to initiate the appropriate workflow for taking them offline. With the information collected using Ordr, organizations can come up with a comprehensive plan to replace these prohibited devices based on the quantity, location and impact.
Step 3
After the prohibited devices are replaced, the new devices will automatically show up in Ordr and the replaced prohibited devices will be noted as “Offline” and can be deleted from the UI. This completes the device replacement workflow.
Additional Considerations
Bring Your Own Device (BYOD) presents a unique challenge. If the organization allows for BYOD to use internal resources, then blocking these prohibited devices is advisable. Ordr has the capability to monitor these devices and can work with Network Access Control (NAC) tools like Cisco ISE and Aruba ClearPass to block these prohibited devices from using the internal resources.
To stay in compliance, continuous monitoring is essential. This can be accomplished with an Ordr and Computerized Maintenance Management System (CMMS) integration. If Ordr discovers a new prohibited device, workflows can be setup in CMMS to alert users to take remediation action.
For more information on how Ordr can help you identify and manage vulnerabilities for any connected device, please contact info@ordr.net.

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud



