(Updated on November 10th with new Ordr capabilities)
On October 26th, OpenSSL Project a critical vulnerability associated with OpenSSL versions 3.0 and higher. The version released on November 1st — OpenSSL version 3.0.7 —addresses this vulnerability.
- CVE-2022-3602 is an arbitrary 4-byte stack buffer overflow that could trigger crashes or lead to remote code execution (RCE).
- CVE-2022-3786 can be exploited by attackers via malicious email addresses to trigger a denial-of-service state via a buffer overflow.
-
These vulnerabilities were downgraded from critical to as high (CVSS score 8.8 from 9.0) on November 1st.
Here is what you need to know about this critical vulnerability:
What is OpenSSL?
OpenSSL is a widely used open-source cryptography utility implemented to keep secure the web traffic exchange between a client and server. It is used to generate public and private keys, install SSL/TLS certificates, verify certificate information, and provide encryption.
Most web servers across the internet and within Intranets use SSL certificates to secure connections and the website being browsed. These certificates are traditionally generated by OpenSSL.
How concerned should we be about this vulnerability?
OpenSSL can be misused if the vulnerable version is in use. The good news is that this vulnerability impacts a very specific version of OpenSSL and patching quickly will address any associated risks.
A flaw in OpenSSL has previously affected businesses. In April 2014, OpenSSL’s Heartbleed flaw was discovered. Numerous web servers, including those running popular websites like Yahoo, included it. Security teams rushed to apply updates because the vulnerability was simple to exploit.
How is this OpenSSL vulnerability exploited?
Both CVE-2022-3602 and CVE-2022-3786 vulnerabilities are prone to buffer overflow attacks that can perform RCE (Remote Code Execution) or expose contents of the memory that contains private keys or proprietary information.
The chances of these vulnerabilities getting abused are low because one of the conditions is a malformed certificate signed by a trusted CA.
The issue lies in the verification process of certificates that OpenSSL performs for certificate-based authentication. The exploitation of the vulnerabilities could allow an attacker to launch a Denial of Service (DoS) or even a Remote Code Execution attack.
Patches for the two weaknesses found in OpenSSL v3.0.0 to v3.06 have now been released.
Which OpenSSL versions are vulnerable?
- OpenSSL versions 3.0 and above are vulnerable.
- OpenSSL 3.0.0, the first stable version of OpenSSL 3.0, was released in September 2021, about one year ago. Any older operating systems prior to 3.0.0 are not impacted by this vulnerability.
- Open SSL version 3.0.0 to 3.0.6 are affected by this vulnerability.
- OpenSSL version 3.0.7 includes the fix for the critical vulnerability.
CRITICAL Severity: This affects common configurations, which are also likely to be exploitable. Among these are significant disclosures of server memory (potentially revealing user information), vulnerabilities that are easily exploitable to compromise server private keys remotely, or situations where remote code execution is possible. We will keep these issues private and release a new version of all supported versions as soon as possible.
HIGH Severity: This includes issues that are of a lower risk than critical, perhaps due to affecting fewer common configurations or which are less likely to be exploitable. These issues will be kept private and will trigger a new release of all supported versions. We will attempt to keep the time these issues are private to a minimum; our aim would be no longer than a month, where this is something under our control.
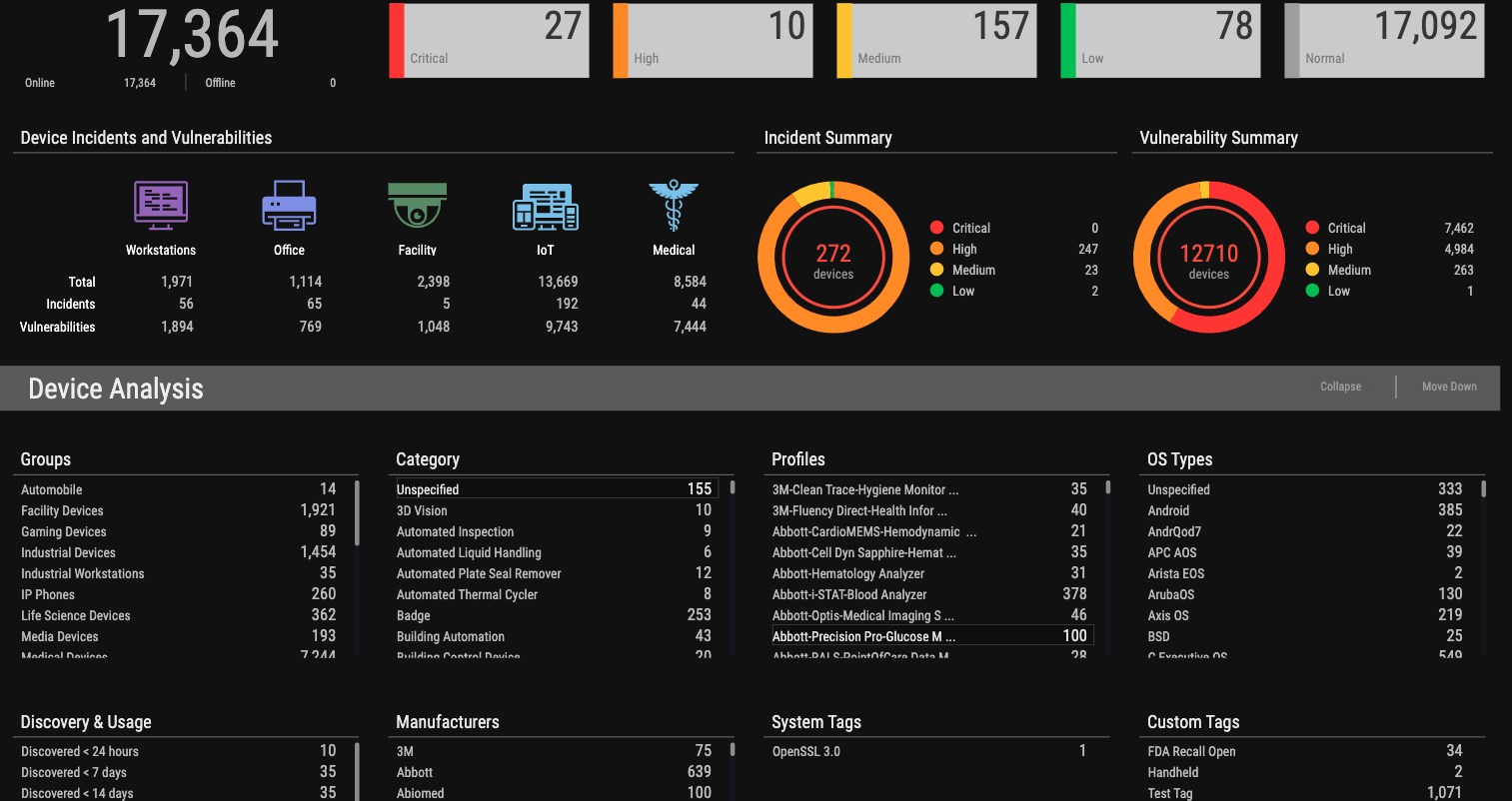
Is the Ordr platform impacted by the OpenSSL vulnerability?
Ordr has reviewed our usage of OpenSSL. This vulnerability does not impact Ordr as we do not use the impacted version.
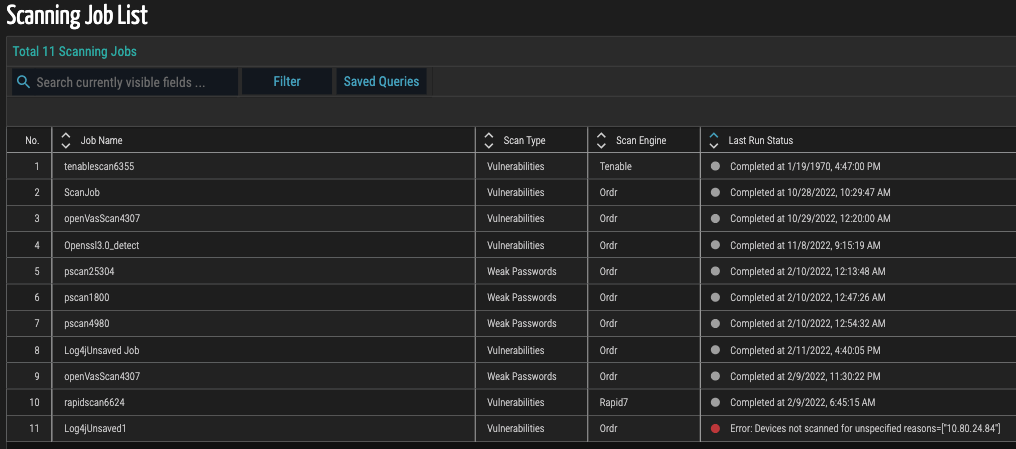
How Ordr can help?
Ordr has added two new capabilities:
-
A new scanner that will detect versions of the OpenSSL that are vulnerable.
-
New IPS signatures that can detect exploits of this OpenSSL vulnerability
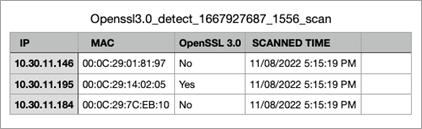
New Ordr Scanner to Detect Vulnerable Versions of OpenSSL
- Ordr scanner uses the following command-line Options:
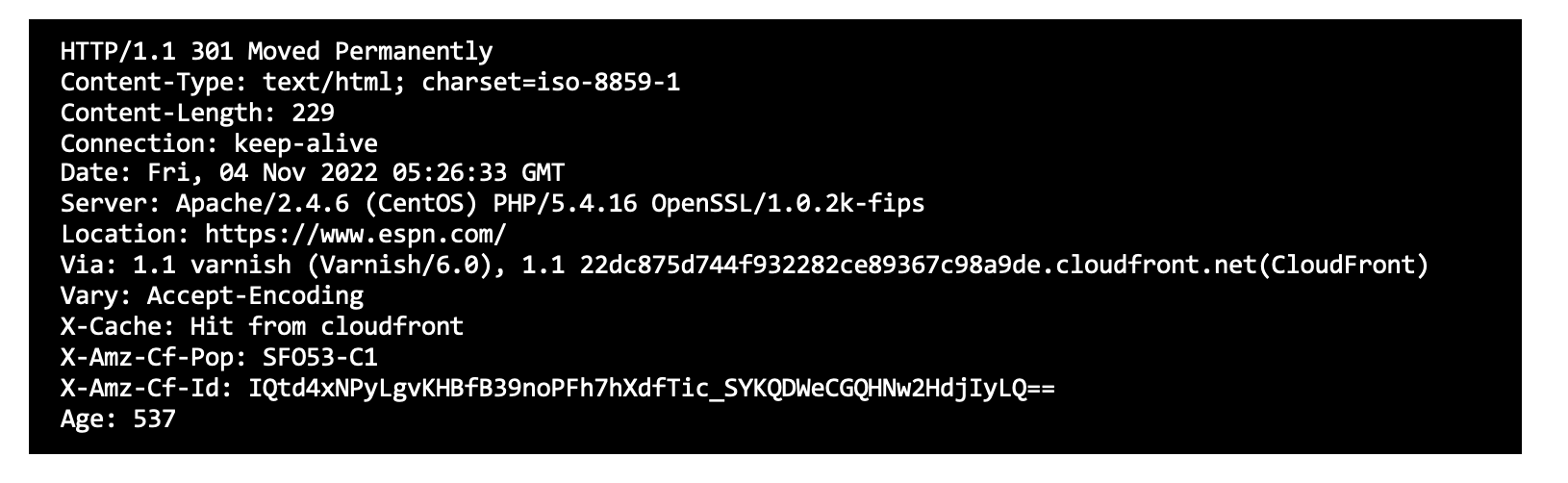
- As servers have an open HTTP port; A curl command is used to connect to them to find the SSL version
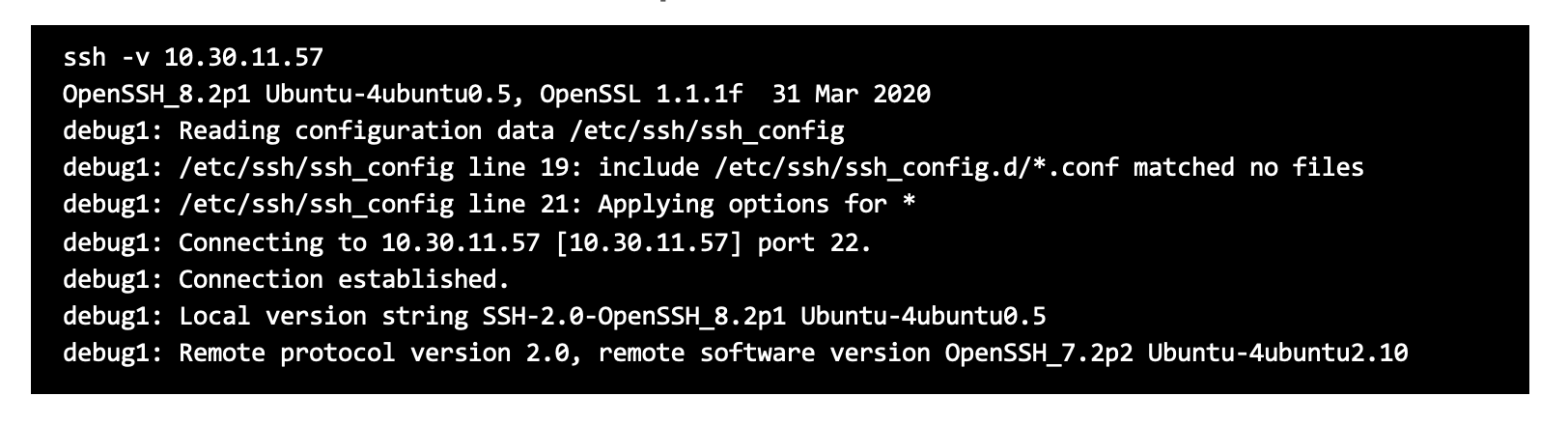
- In cases where clients do not usually have web services, the “ssh” command can be used instead.
- As for a detection method, we use HTTPS headers, SSH headers, and credentialed scans to get the information.
- Some scanners use only authenticated approach that requires full credentials, but Ordr uses an unauthenticated way to get information about Open SSL versions.
- Ordr scanner also uses tools like Nmap to find open ports as a precursor before finding out about the OpenSSL version.
- Example screenshots of detecting Open SSL that is built into the Ordr scanner.
Sample SSL command
Sample SSH command
Packet Parser with IDS Signatures to Detect Exploit Attempts
- While the Ordr scanner detects all the machines that have this vulnerability, the next step is to see if any exploits are exploting this vulnerability.
- There is a parser on the wire that we need to enhance with rules to get versions of TLS, certs, and cryptography.
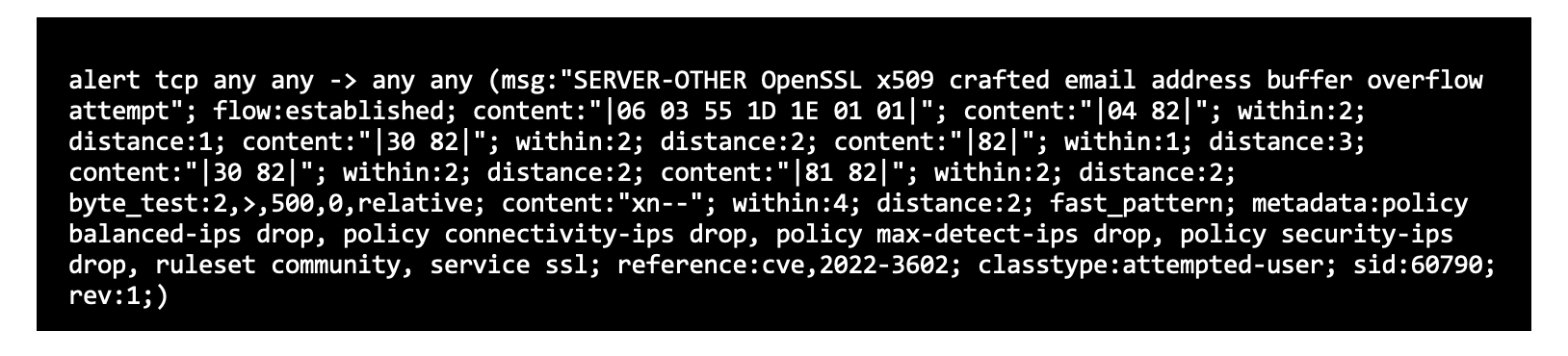
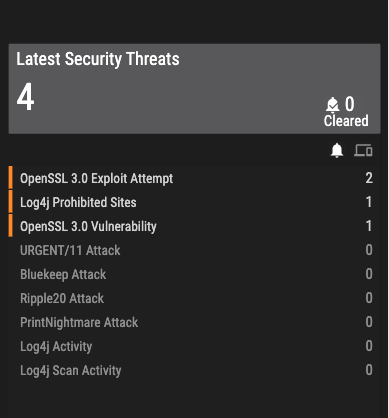
- Ordr has an intrusion detection engine that scans for exploits of this vulnerability with the correct signatures. For example, given below is a signature that would help identify the exploit of this vulnerability.
- CVS-2022-3602 Detection – Detection of this pattern was done using IDS Signatures.
- A buffer overflow can be triggered by sending an X.509 certificate with a specially crafted email address in the “id-on-SmtpUTF8Mailbox” field (OID 1.3.6.1.5.5.7.8.9), resulting in a crash (Denial of Service – DoS) or potentially remote code execution on a vulnerable client or server. Potential opportunities for exploitation can occur if a server requests authentication information after a malicious client connects or if a client connects to a malicious server, which would then make the client vulnerable.
- “OpenSSL x509 crafted email address buffer overflow attempt” is detected with the following signature.
- In the event that there is a malicious activity involving OpenSSL, Ordr has pushed the latest signature to all its customers, and the alarms will be raised.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud




